Enter Network Security Section
In the Telivy Risk Assessment, it is part of the Network Security section.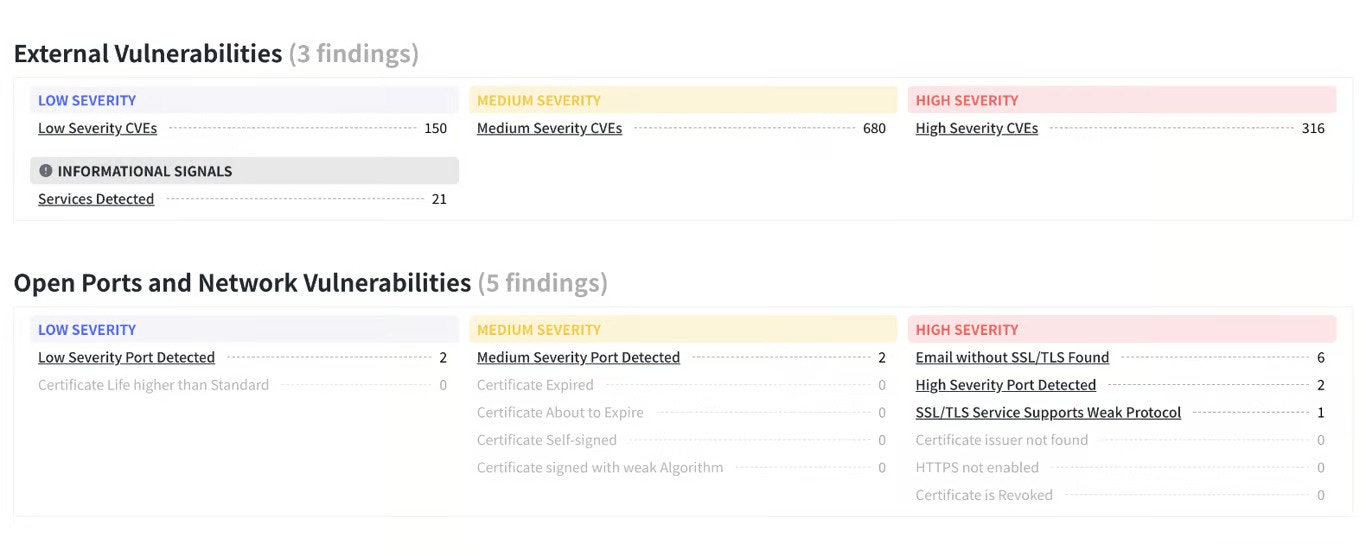

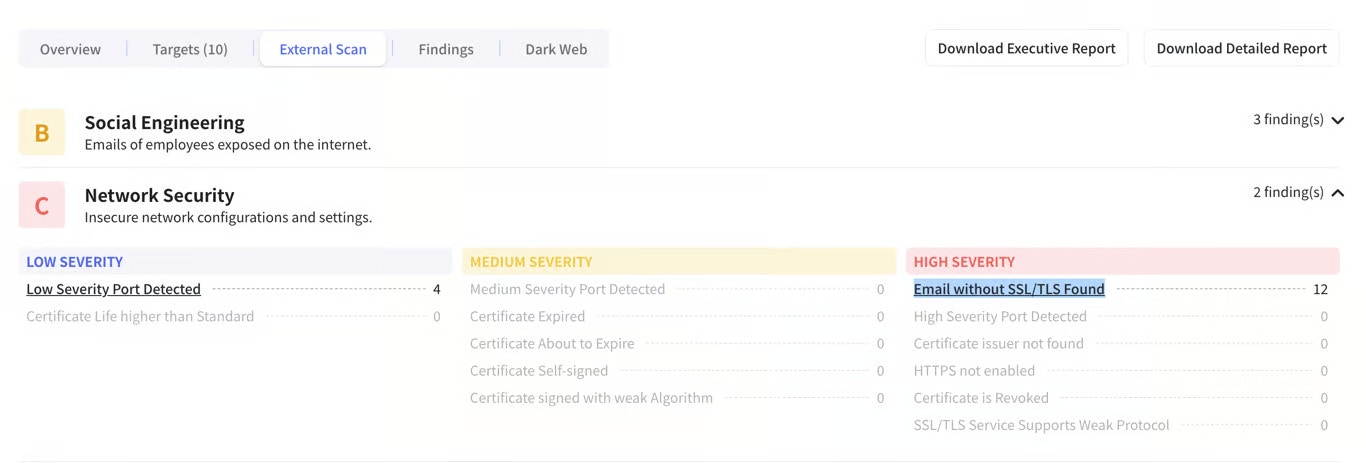
Ports Overview
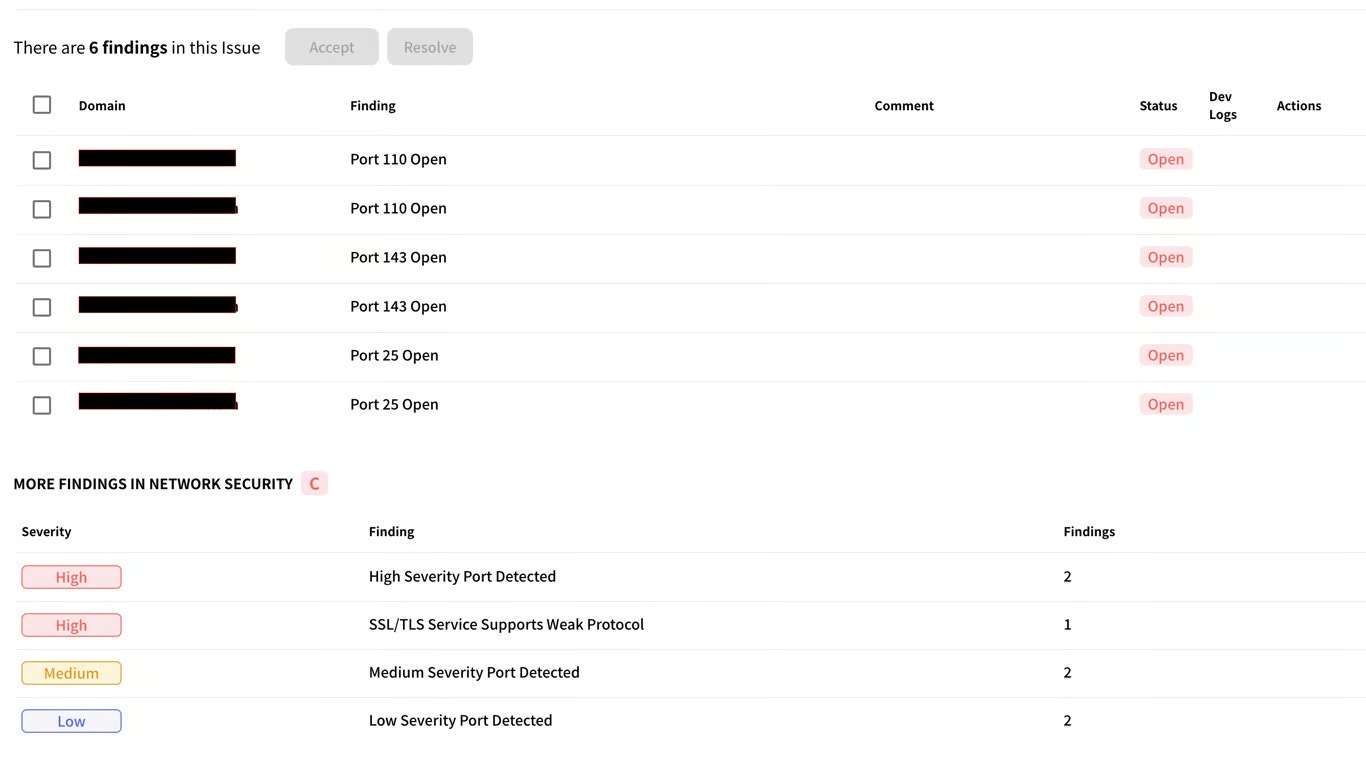
Let’s delve into the different ports that might be usually found in this finding and the associated vulnerabilities and context needed to understand these findings:Port 110 (POP3)
Port 110 (POP3)
This port is used by the Post Office Protocol (POP3) for retrieving emails from a server.Vulnerability: POP3 transmits data in plain text, making it susceptible to eavesdropping and password theft. However, if users enable POP3 over SSL (POP3S on port 995), the communication becomes encrypted. Additionally, if emails are already secured on the server and users practice good password hygiene, the risk might be lower.Context: Consider whether POP3 is still actively used, if SSL is enabled, and the sensitivity of the emails retrieved. Consider switching over to POP3S and closing this port.
Port 143 (IMAP)
Port 143 (IMAP)
This port is used by the Internet Message Access Protocol (IMAP) for accessing and managing emails on a server.Vulnerability: Similar to POP3, unencrypted IMAP (on port 143) transmits data in plain text. Using IMAP over SSL (IMAPS on port 993) mitigates this risk. Additionally, the level of access granted to users through IMAP (read-only or full management) impacts the potential damage.Context: Assess whether IMAP is actively used, if SSL is enabled, the user access levels, and the sensitivity of the emails stored. Consider switching over to IMAPS on port 993.
Port 25 (SMTP)
Port 25 (SMTP)
This port is used by the Simple Mail Transfer Protocol (SMTP) for sending emails.Vulnerability: An open SMTP server can be exploited by spammers to send out malicious emails through your server. Additionally, weak authentication mechanisms can allow unauthorized access for sending emails.Context: Evaluate if your own SMTP server is necessary, if strong authentication (e.g., STARTTLS, SASL) is enforced, and whether reputation management tools are used to prevent abuse. This port is needed for anyone on the public internet to send emails.