Requirements
To get login and security data from M365, a Microsoft Entra ID P1 (NCE) license and Global admin is required. This license allows us to retrieve monitor login statistics like location and MFA status from Microsoft. This license comes with audit logging which enables us to monitor M365 security. Check out plans, cost, and features here.Configuration
To configure the M365 security, go to your Risk Assessment > Configuration > Configure Microsoft 365 and follow the steps to connect your M365 admin account. Make sure you have the required licenses as described in the previous sections.

M365 Security Score
Understanding Your Score
Understanding Your Score
Telivy presents your M365 security score in a clear, actionable format. You’ll see an overall score and detailed breakdowns for different security domains, a benchmark on how your peers are scoring helping you identify areas for improvement. The M365 security score is determined based on your M365 security configurations. The dashboard provides possible improvements to increase your score.
Tracking Progress
Tracking Progress
Monitor your security score over time to measure the effectiveness of your security efforts. Telivy helps you visualize trends and celebrate improvements.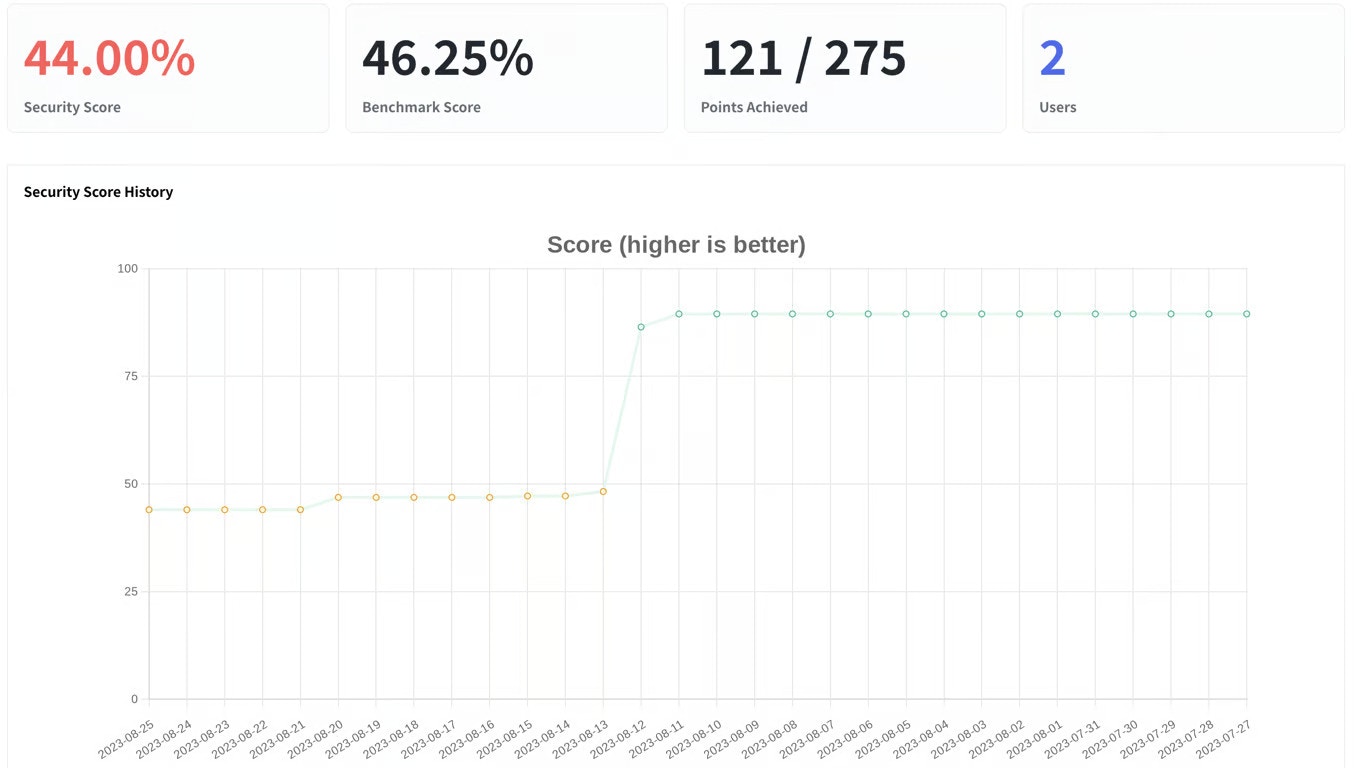

Prioritizing Improvements
Prioritizing Improvements
Telivy goes beyond just showing your score. It provides specific recommendations tailored to your environment and the change in the score by completing those actions.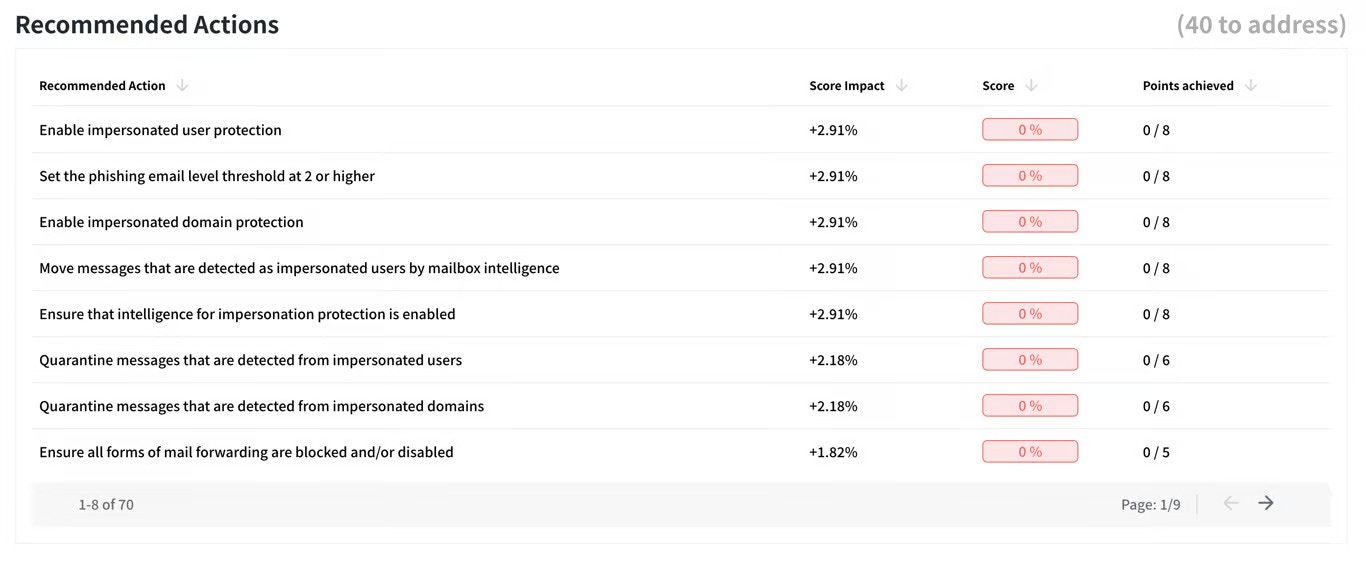

Account Status
Ensuring User Account Security
Ensuring User Account Security
Telivy displays the MFA status of all user accounts within your organization. This allows you to easily identify accounts without MFA enabled, a critical security control.
Auditing User Accounts
Auditing User Accounts
Verify existing user accounts in M365 to ensure unauthorized.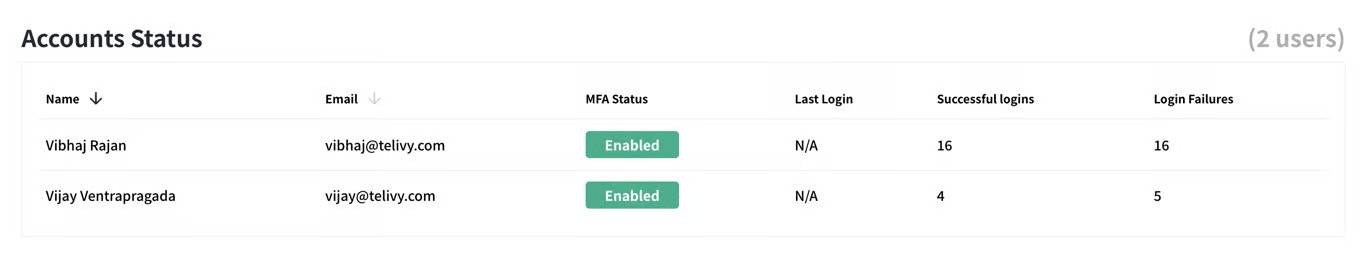

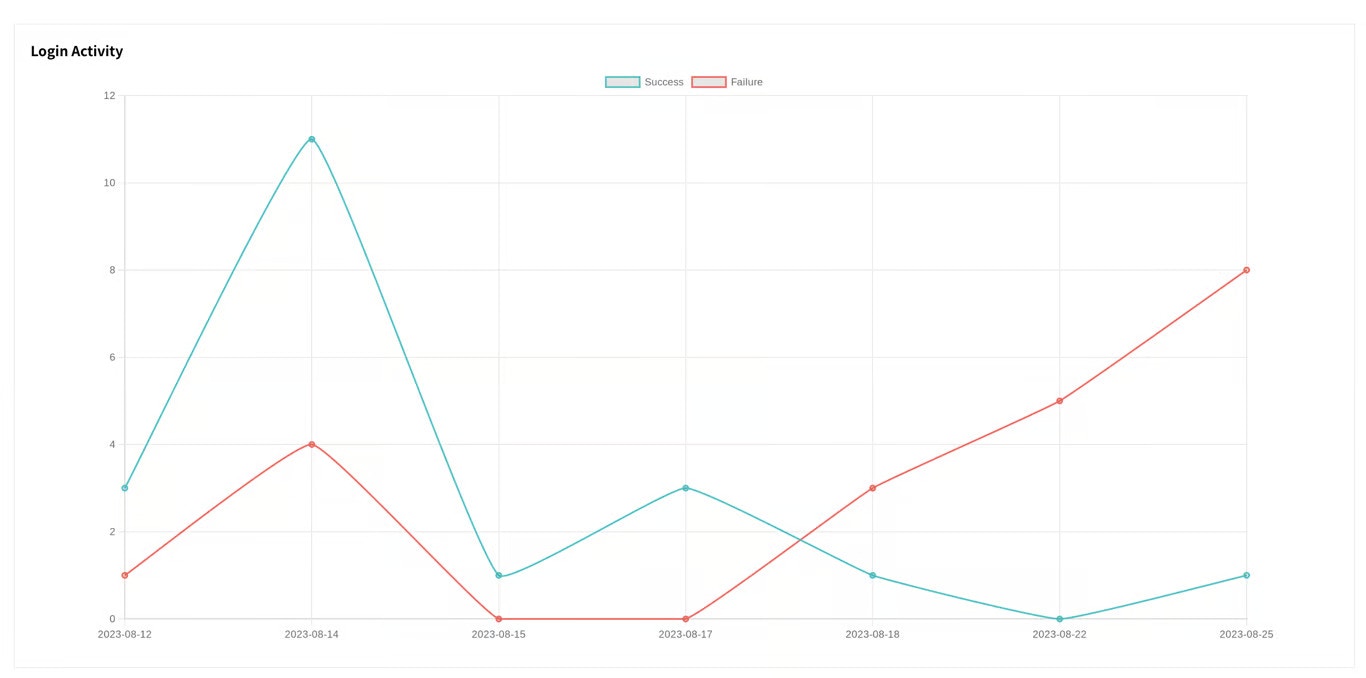
Login Successes And Failures
Monitoring Suspicious Activity
Monitoring Suspicious Activity
Telivy tracks login attempts for all user accounts, highlighting successful and failed logins. This helps you identify potential breaches or unauthorized access attempts.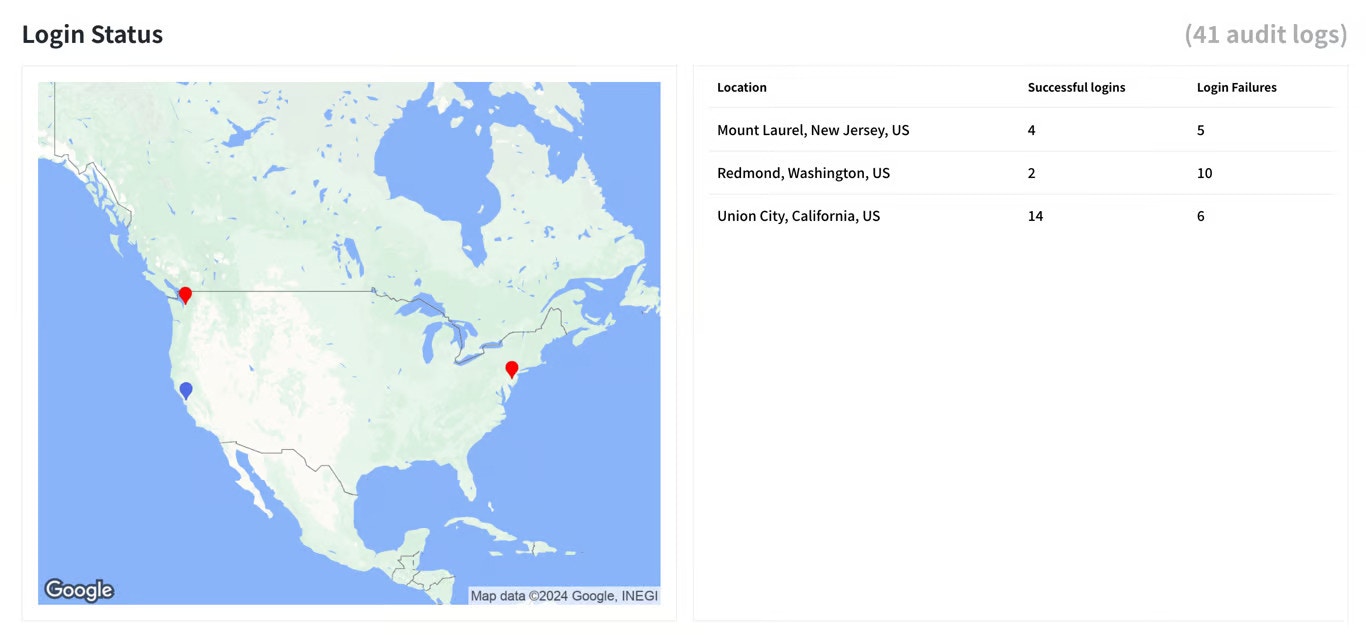

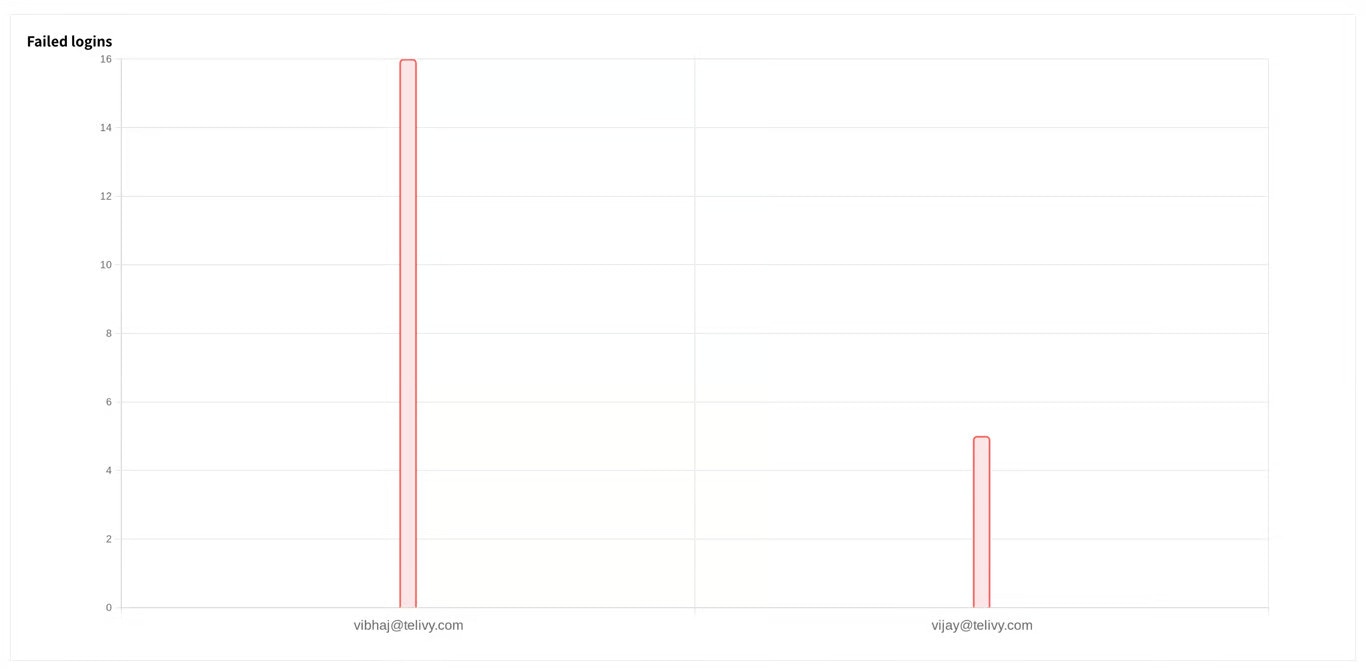
Investigating Suspicious Logins
Investigating Suspicious Logins
Telivy provides information for each login attempt for all user agents. This equips you to investigate suspicious activity thoroughly.